Single Sign-On with Okta
IDrive® e2 users can access their accounts using Single Sign-On (SSO). Administrators can choose a SAML 2.0 identity provider (IdP) to enable login to IDrive® e2 without the need to remember an additional password.
To setup Single Sign-On (SSO) with Okta, the admin needs to:
Create an app on Okta Console
Create an app on Okta console and use it as an identity provider for SSO.
To create the app,
- Log in to the Okta console using your Okta account credentials.
- Click 'Admin' to navigate to the admin console.
- Navigate to 'Dashboard' > 'Applications' > 'Applications'.
- Click 'Browse App Catalog'.
- Enter IDrive® e2 in the search bar.
- Click 'Add integration'.
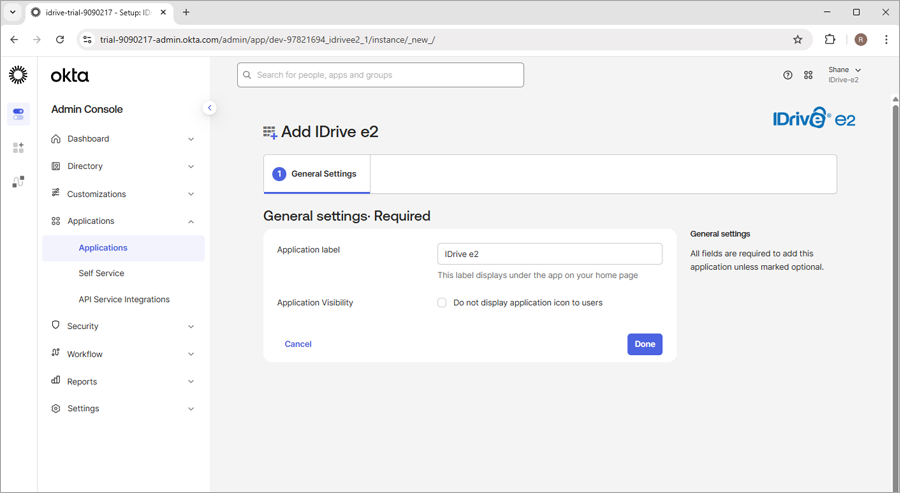
- Go to 'General Settings' and click 'Next'.
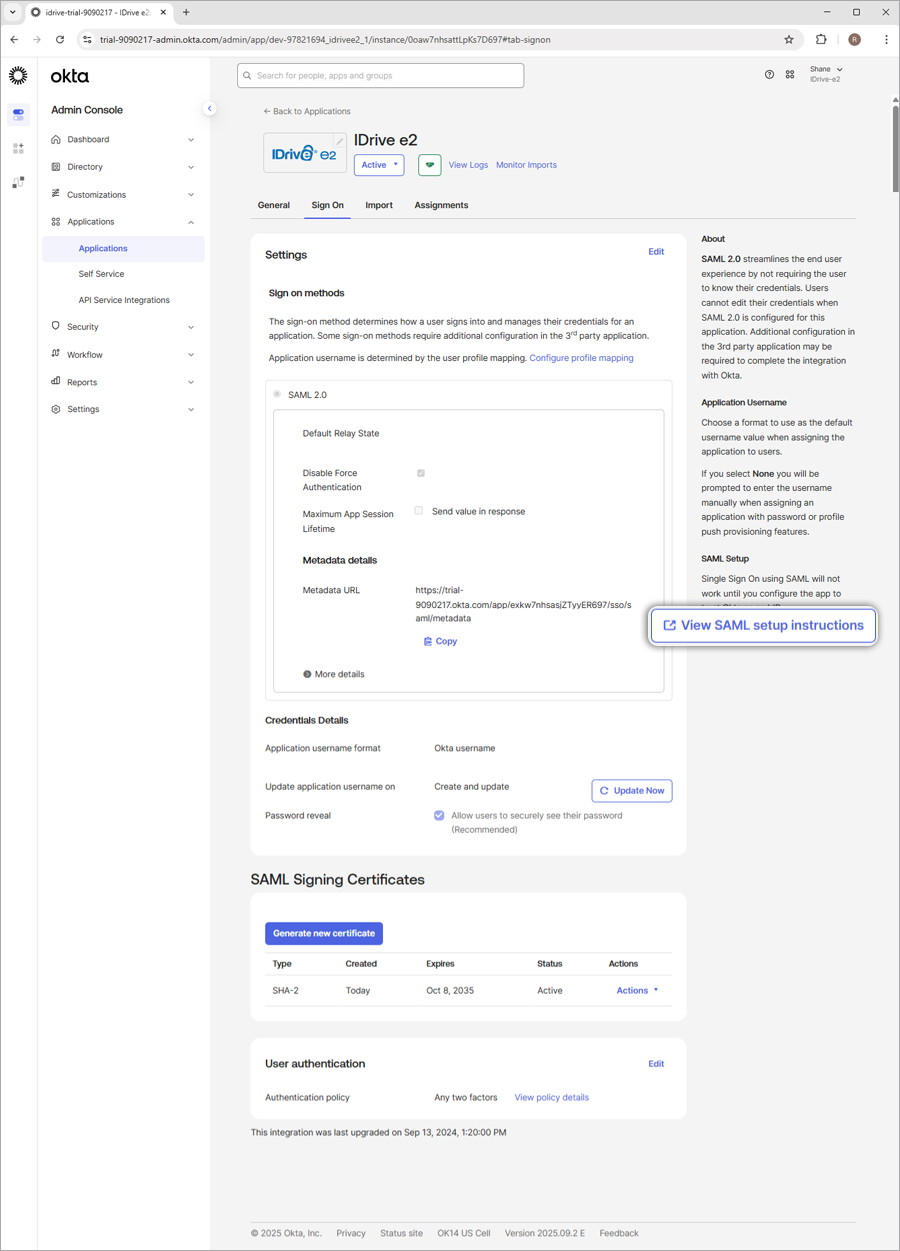
- Go to 'Sign-On' Options, select SAML 2.0, and click 'View Setup Instructions'. You will be directed to a web page where you will find SAML 2.0 Single Sign-On Login URL, Issuer URL, and the X.509 Certificate. Copy these and paste them on IDrive® e2 SSO settings.
Assign users
To enable SSO for user accounts, admin needs to assign users to the new app on Okta console.
To assign users,
- Launch the new app on Okta console.
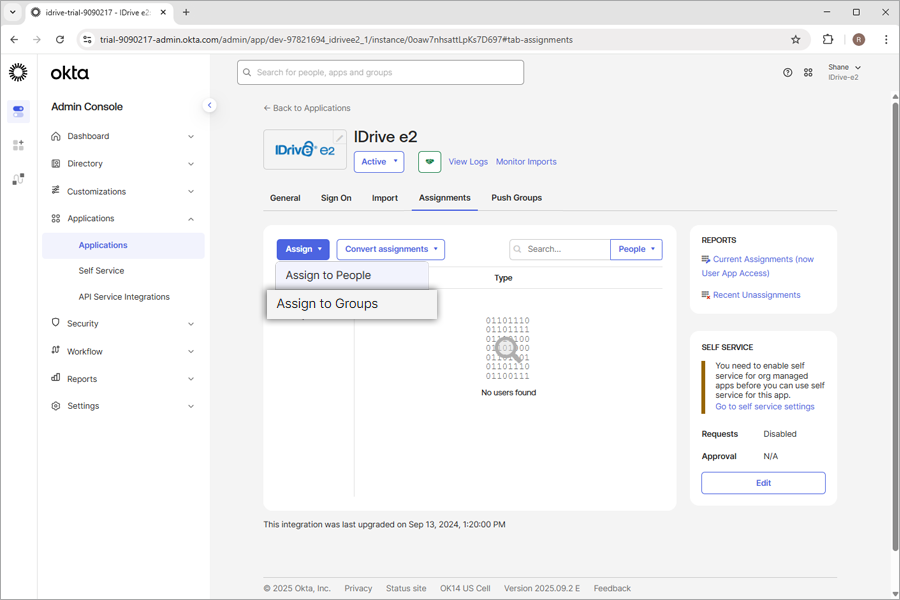
- Click 'Assign'.
Configure IDrive® e2 account for Single Sign-On (SSO)
Admin needs to provide the received SAML 2.0 URLs and Certificate in the Single Sign-On application from the IDrive® e2 web interface.
To configure SSO,
- Sign in to IDrive® e2 via web browser.
- Navigate to the 'Dashboard' > 'Settings' > 'Single Sign-On (SSO)'.
- Enter a name for your SSO profile.
- Enter the Issuer URL and SSO Endpoint.
- Upload the X.509 certificate received from your IDP.
Note: X.509 certificate should only be in X.509 certificate should only be in .pem, .txt, .cer, and .cert format. - Click 'Configure Single Sign-On'
You will receive a confirmation email once SSO is enabled for your account.
Single Sign-On provisioning setup - Okta (SCIM)
Administrators of IDrive® e2 can now set up provisioning for their users and groups from the identity provider. IDrive® e2 supports the SCIM (System for Cross-domain Identity Management) provisioning method for this purpose.
To setup Single Sign-On (SSO) provisioning with Okta, the admin needs to:
- Generate SCIM provisioning token with IDrive® e2 account
- Configure SCIM provisioning
- Assign users / groups
Generate SCIM provisioning token with IDrive® e2 account
Admin needs to generate and use the SCIM (System for Cross-domain Identity Management) provisioning token to sync all the users linked with their IdP to the IDrive® e2 account.
To generate a token,
- Sign in to IDrive® e2 via web browser.
- Navigate to the 'Dashboard' > 'Settings' > 'Single Sign-On (SSO)'.
- In the SSO section, click the 'Generate Token' button under 'Sync users from your identity provider' to generate a token.
- Click the 'Copy Token' button to copy and save the token for future reference.
The token will be required to sync all the users linked with your IdP to your IDrive® e2 account.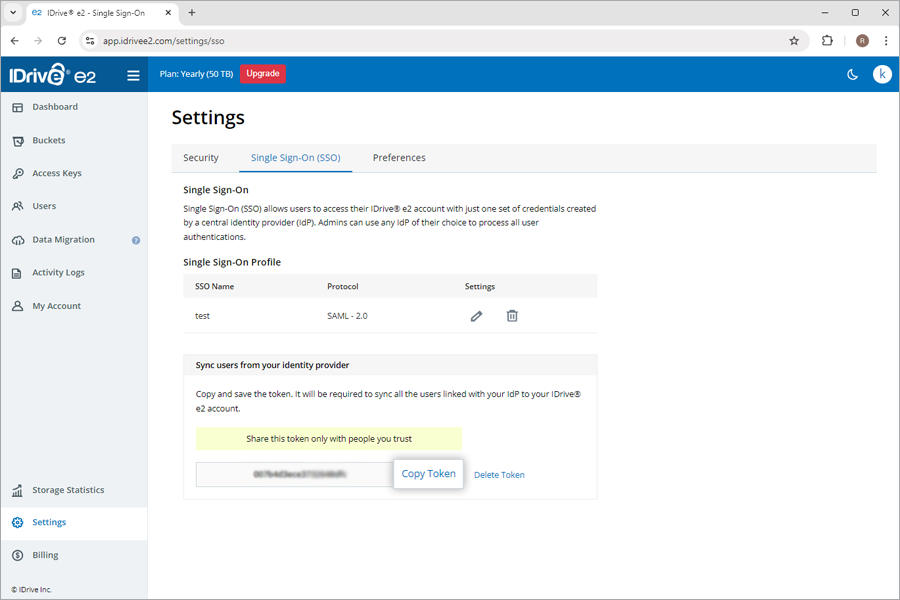
- Configure the following SCIM User provisioning URL in your IdP:
https://api.idrivee2.com/api/sso/user_provisioning
Configure SCIM provisioning
Once the app is created, admin can configure their account for SCIM provisioning.
To configure SCIM provisioning,
- Log in to the Okta console using your Okta account credentials.
- In the 'Applications', click on the newly created app.
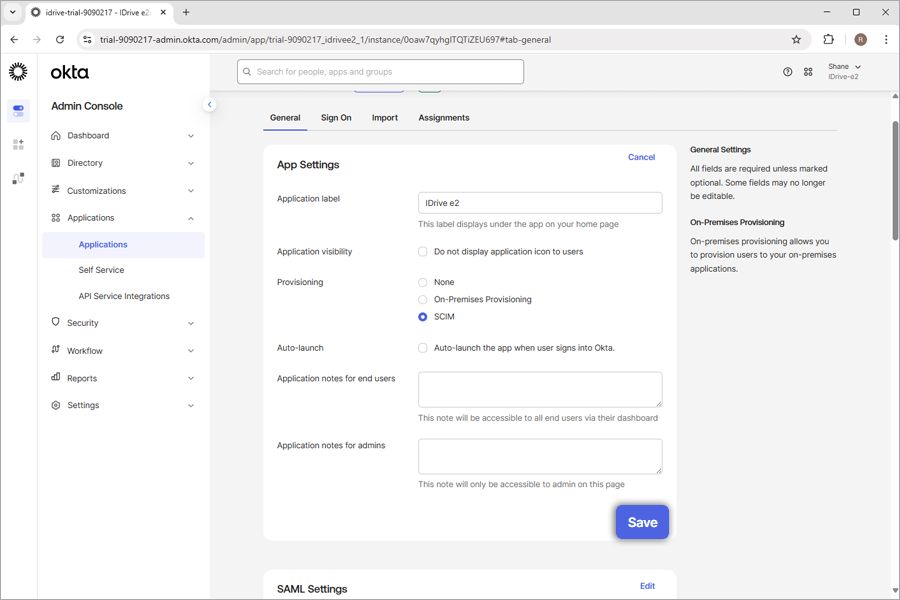
- Navigate to 'General', click 'Edit' corresponding to the 'App Settings', and select 'SCIM'. Click 'Save'.
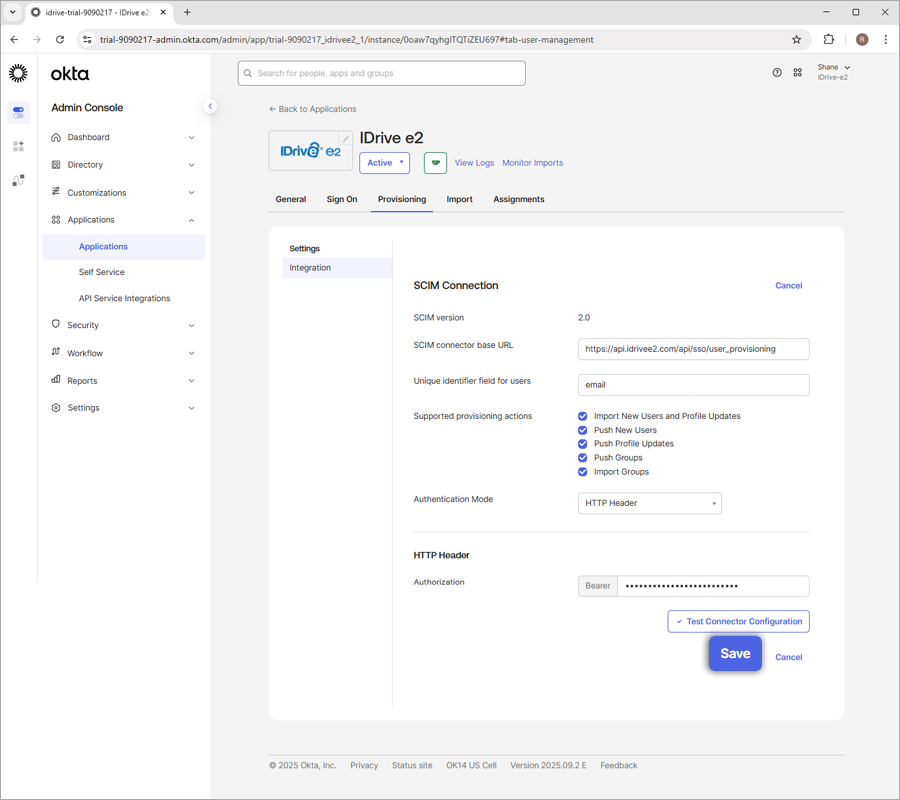
- Go to the 'Provisioning', click 'Edit' against the 'SCIM Connection' and modify the required changes as below:
- SCIM connector base URL:
https://api.idrivee2.com/api/sso/user_provisioning - Unique identifier field for users: email
- Supported provisioning actions: Click and enable the below options:
- Push New Users
- Push Profile Updates
- Push Groups
- Authentication Mode: HTTP Header
- Authorization: Enter the SCIM provisioning token generated on your IDrive® e2 account
- SCIM connector base URL:
- Click 'Save'.
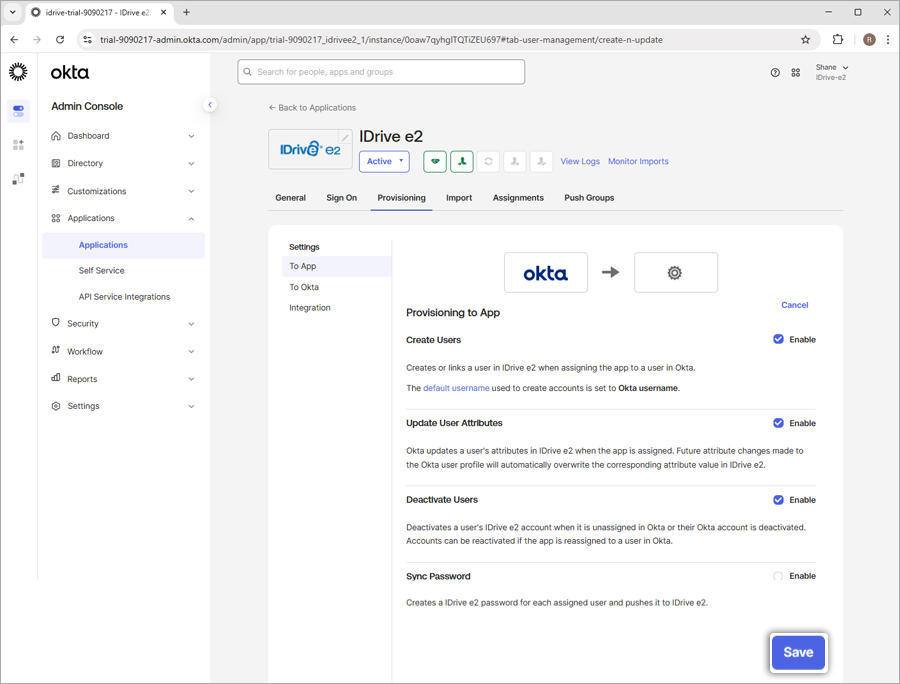
- Under the 'To App' tab, click 'Edit' against the 'Provisioning to App' option.
- Click the 'Enable' to enable the below options:
- Create Users
- Update User Attributes
- Deactivate Users
- Click 'Save'.
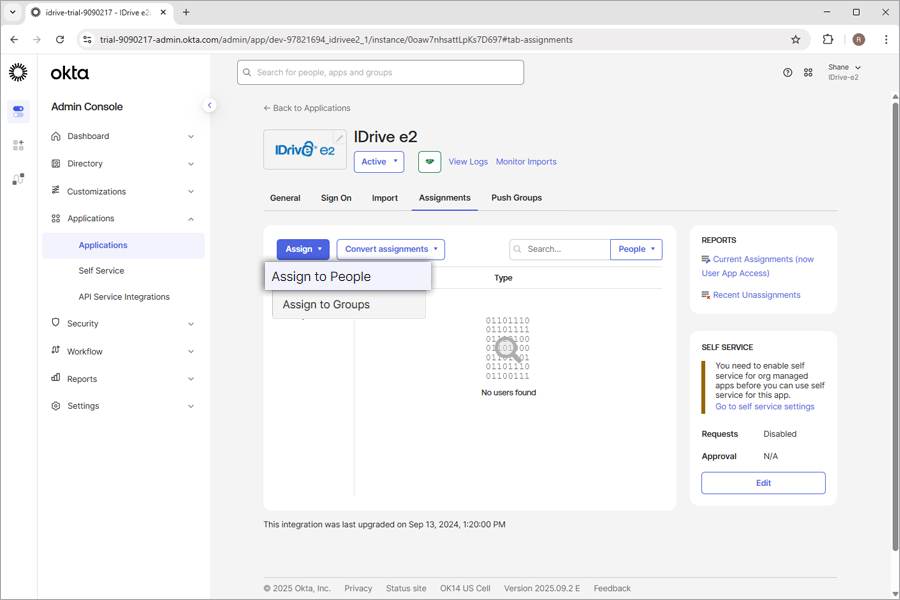
Assign users
To start provisioning, an admin needs to assign users/groups to the application and push groups.
To assign users,
- Launch the new app in Okta console.
- Go to the 'Assignments', click 'Assign', and select 'Assign to People' or 'Assign to Groups' to provision users or users in the group, respectively.
This will provision users and users in the group.
Note: If you want to add new users, go to 'Directory' > 'People' and click 'add person'.