Related Links
- Developer's Guide
- Endpoints and Access Keys
- Third-Party Tools
- Veeam®
- Veeam® 12 Direct-to-Cloud
- MSP360
- MSP360 Cloudberry
- MSP360 CloudBerry Explorer
- MSP360 Managed Backup Service
- Ahsay
- Acronis Cyber Protect Cloud
- Anchorpoint
- AirLiveDrive
- Archiware P5
- Arcserve
- Arcserve ImageManager
- Arq Backup
- BackupAssist
- Bunny.net
- ChronoSync
- Cloudmounter
- Cloudflare
- Comet
- Couchbase
- cPanel Backup
- CrossFTP
- CuttingRoom
- CubeBackup
- Cyberduck
- Dell
- Dropshare
- Duplicacy
- Duplicati
- EditShare
- ExpanDrive
- Fastly CDN
- Files.com
- Filezilla Pro
- Flexify.IO
- GoodSync
- Hammerspace
- Hedge OffShoot
- Hitachi Content Platform
- iconik
- Iperius Backup
- iRODS
- Jet Backup5
- LucidLink
- Milestone XProtect
- Mountain Duck
- MultCloud
- /n software S3 Drive
- NAKIVO Backup and Replication
- Nextcloud
- NirvaShare
- NovaBACKUP
- odrive
- Photos+ Cloud Library
- PureStorage
- qBackup
- QNAP
- Quest Rapid Recovery
- Rclone
- Restic
- Retrospect
- S3 Browser
- S3cmd
- S3Drive
- s5cmd
- S3FS
- SFTPCloud
- SimpleBackups
- Snowflake
- SyncBackPro
- Syncovery
- Synology Hyper Backup
- Synology Cloud Sync
- Transmit
- TrueNAS® CORE
- UpdraftPlus Backup
- Vantage Gateway
- Veeam® Backup for Microsoft 365
- Vembu BDR Suite
- Veritas Backup Exec
- WinSCP
- Windows Network Drive
- CNAME Record Guide
- API Documentation
Integrate Acronis Cyber Protect Cloud with IDrive® e2
Acronis Cyber Protect Cloud is designed to deliver cyber protection efficiently and securely. Use Acronis Cyber Protect Cloud with IDrive® e2 to combine data backup with AI-based antivirus, anti-malware, and endpoint protection. Learn more about Acronis Cyber Protect Cloud.
Prerequisites:
Before uploading files using Acronis Cyber Protect Cloud, you require:
- An active IDrive® e2 account. Sign up here if you do not have one.
- A bucket in IDrive® e2. See how to create a bucket.
- Valid Access Key ID and Secret Access Key. Learn how to create an access key.
- A valid Acronis Cyber Protect Cloud account.
Configure Acronis Cyber Protect Cloud with IDrive® e2
- Sign in to Acronis Cyber Protect Cloud console.
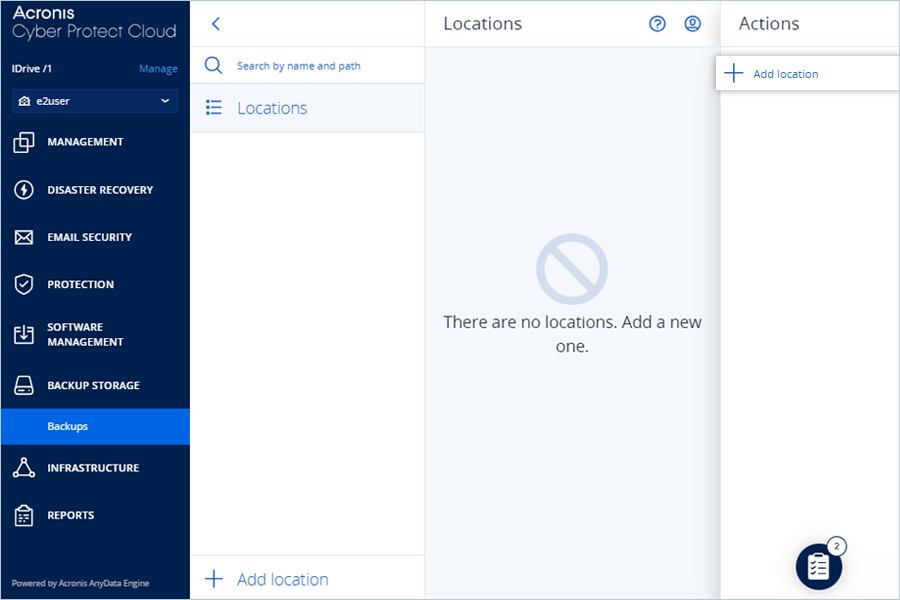
- Navigate to BACKUP STORAGE > Backups.
- Click Add location in Actions.
- Go to Public cloud and select S3 compatible as Cloud from dropdown.
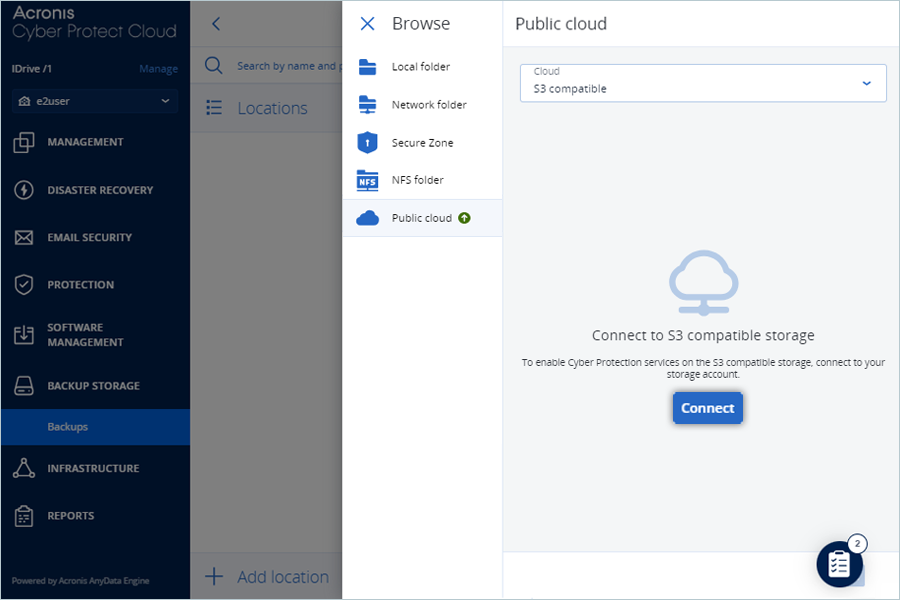
- Click Connect.
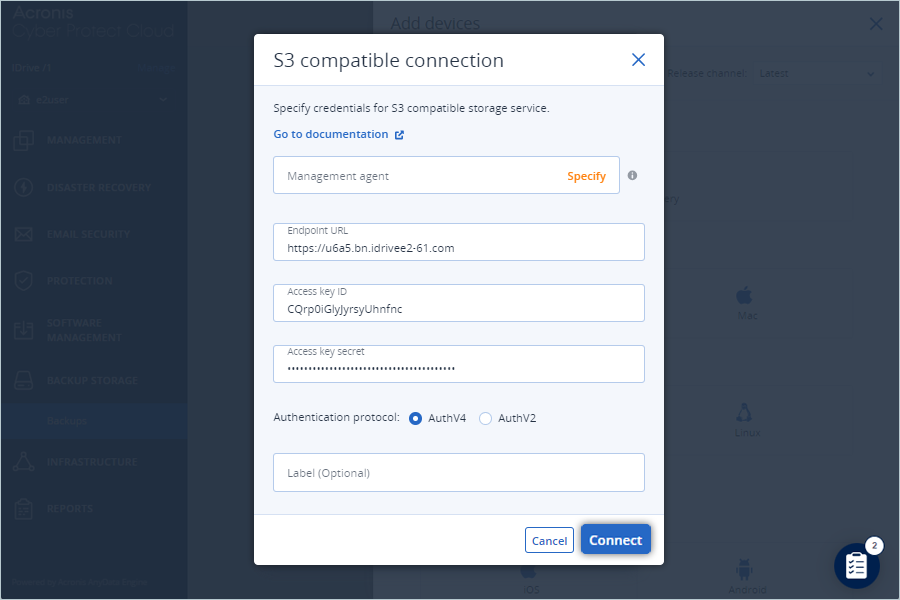
- In S3 compatible connection window, enter your e2 storage credentials:
- Enter the IDrive® e2 storage end-point as Endpoint URL.
- Enter the IDrive® e2 Access Key as the Access Key ID.
- Enter the IDrive® e2 Secret Access Key as the Access key secret.
- Select AuthV4 as the Authentication protocol.
- Click Connect.
- Under Add devices, select the desired device (e.g., Windows Workstation). The download will start automatically.
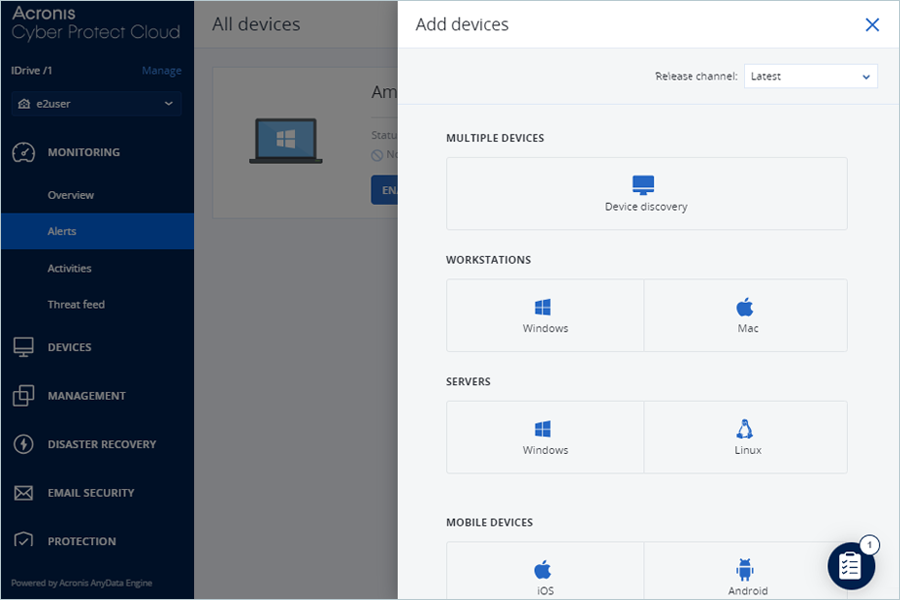
Note: Install the downloaded file. After installation, the device will appear under All devices.
- Under All devices, click ENABLE PROTECTION for the newly added device.
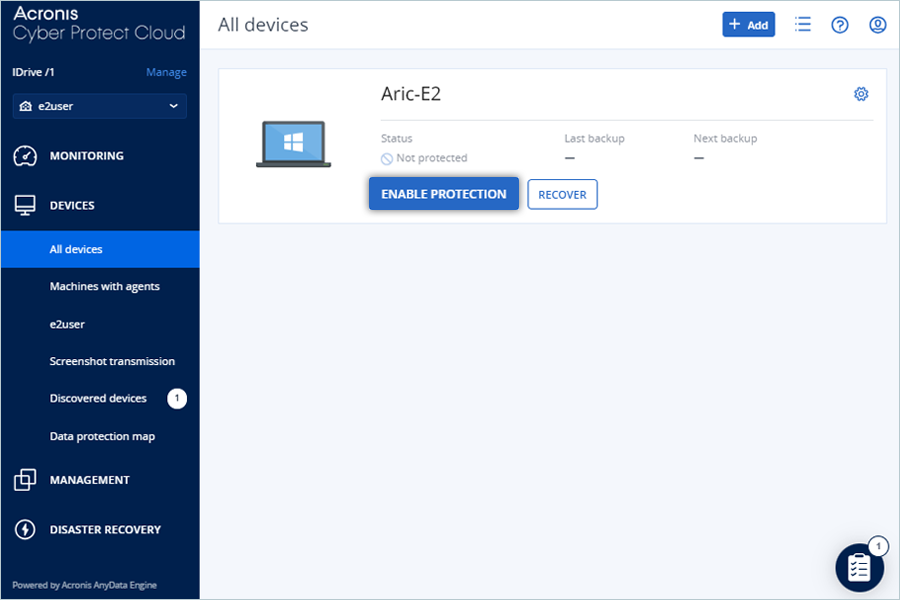
- In the slider window, click Create plan from dropdown and select Protection.
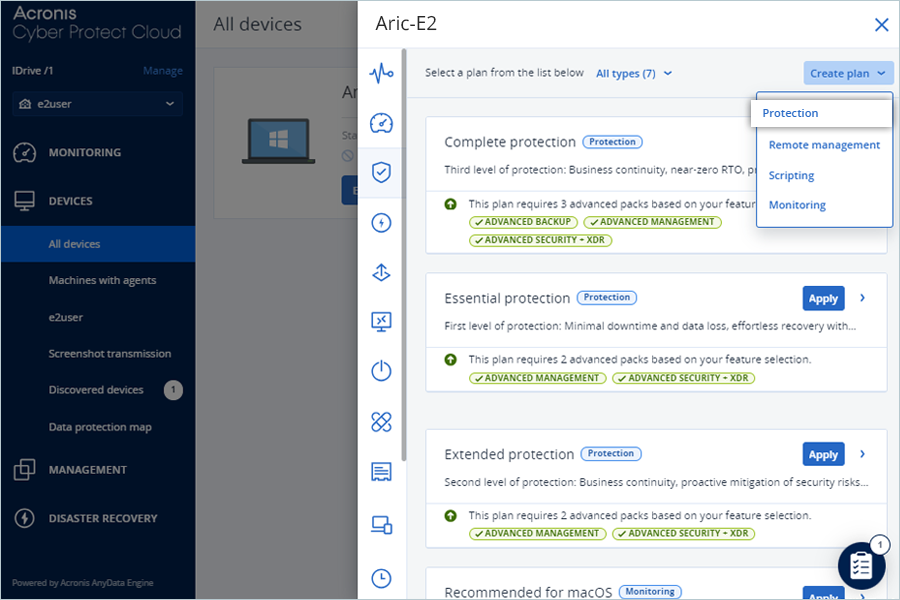
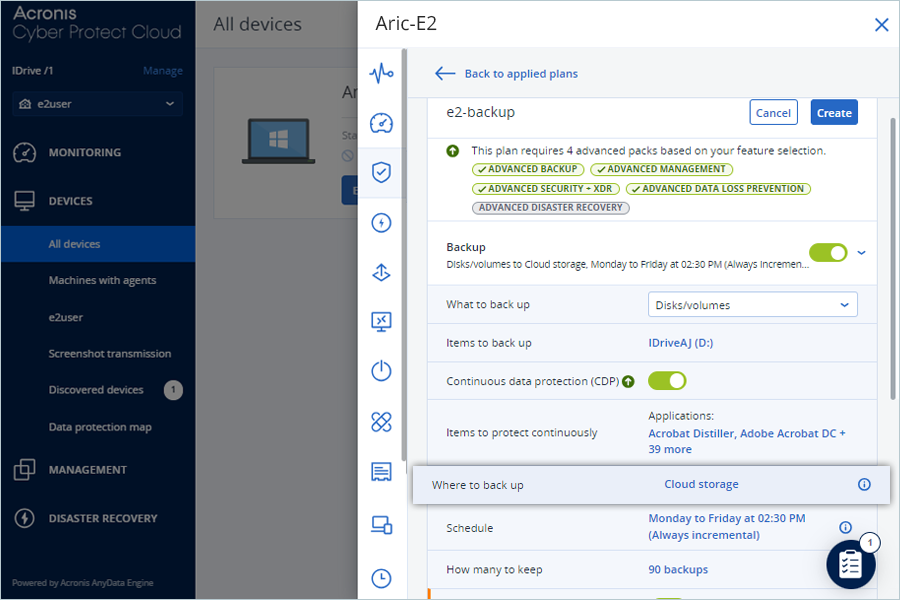
- Enter a name for the Protection Plan.
- Select items for backup (local drive/folder/files) by clicking on Items to backup.
- Click Where to back up.
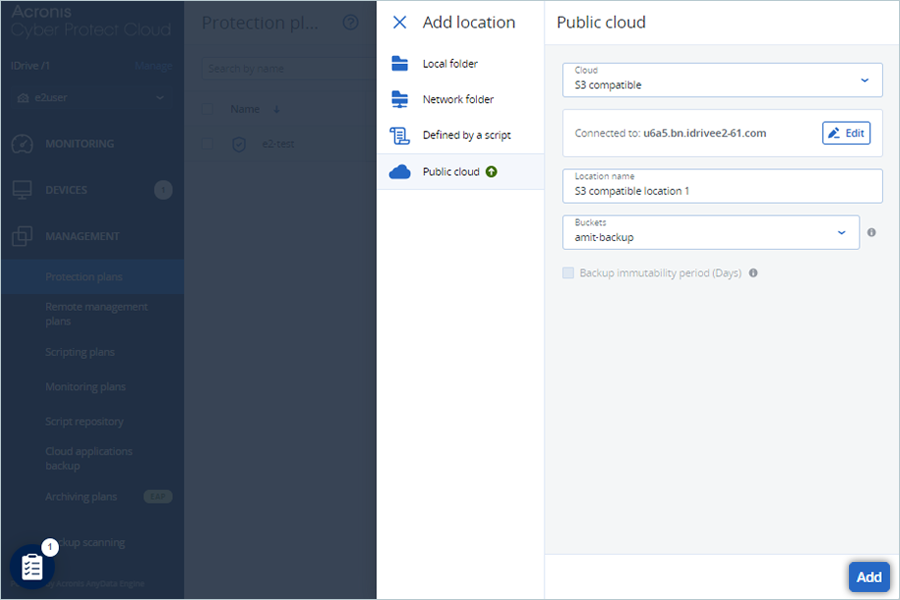
- Select the added Cloud storage or repeat steps from 3 to 6 to add a new location.
- Click Add.
- Click Confirm.
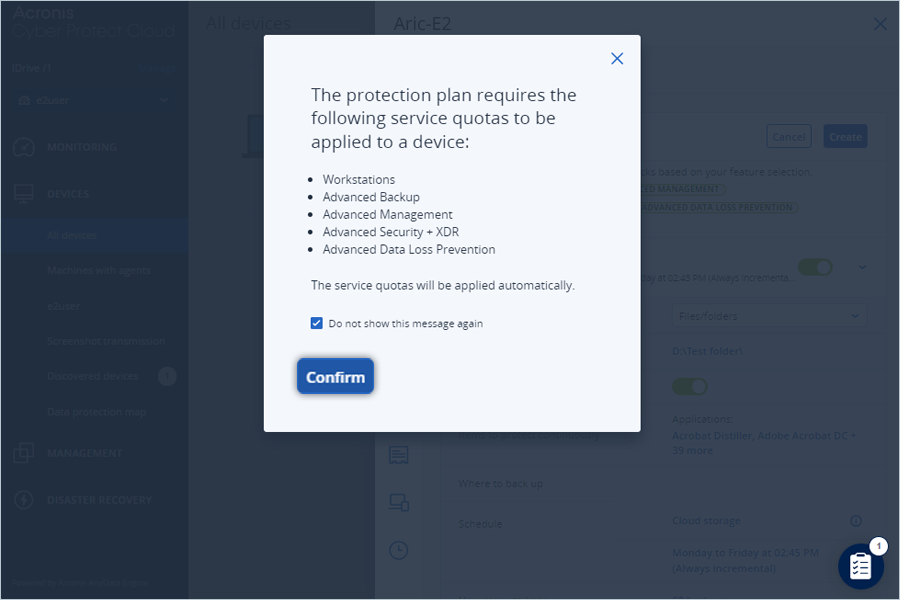
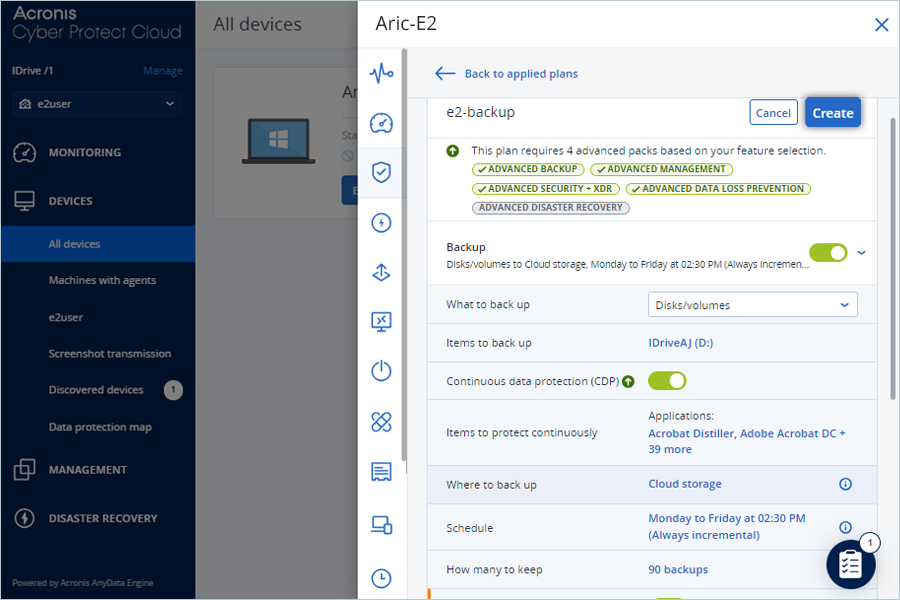
- Click Create.
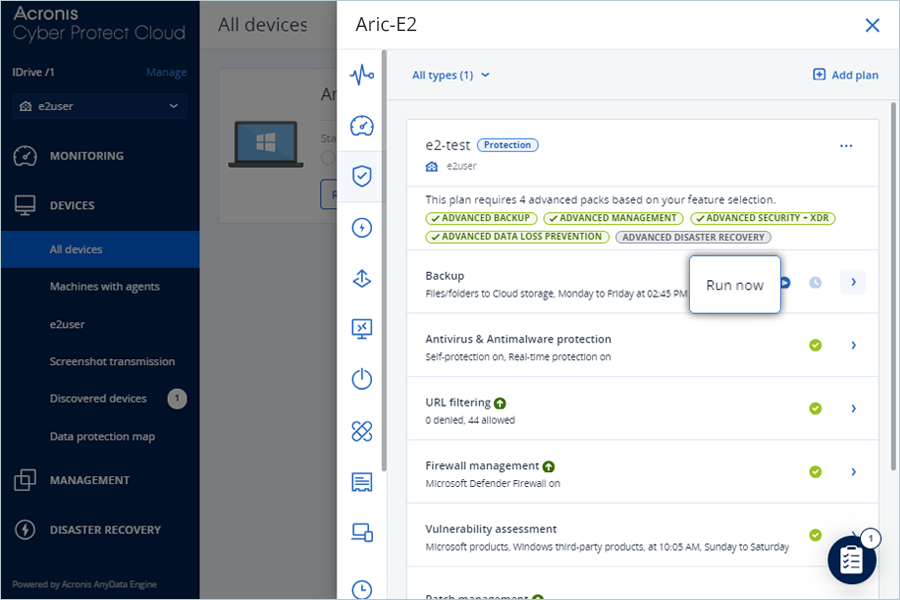
- Click Run now to initiate the backup process.
Note: Data restoration is handled by your specific backup solution provider and is affected by multiple variables that are unique to your environment. For application-related enquiries/support, it is strongly recommended you seek guidance from the technical team of your backup solution provider.